PUBLISHED ONMay 28, 2018 2:11 AM

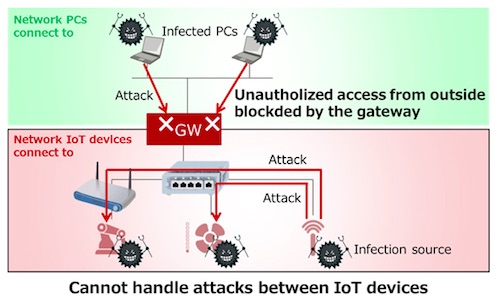 |
Figure 1: Existing technology: Network separation by a gateway |
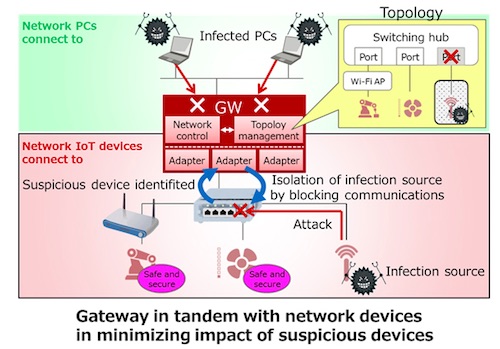 |
Figure 2: Newly developed method |
KAWASAKI, Japan, May 28, 2018 - (JCN Newswire) - Fujitsu Laboratories Ltd. today announced the development of network control technology that can securely operate IoT devices installed on-site. Sensors, manufacturing equipment, and other IoT devices connected to networks in on-site environments such as factories lack the capability for authentication or virus checking, leaving them open to malware attacks that result in stoppages in factory operations. This is a global problem, and existing anti-virus software often cannot be installed in IoT devices due to CPU and memory capacity restrictions, and many existing devices are exposed to threats from cyberattacks. Fujitsu Laboratories has now developed technology that analyzes and manages the interconnectivity between IoT devices and network devices, based on operating information collected in gateways, responding to successive changes in network structure to identify the communications of IoT devices behaving suspiciously. In addition, Fujitsu Laboratories developed technology to efficiently control communication blocks. If an IoT device infected with malware were to attack other devices, for example, these technologies could detect that communication by comparing ordinary communication routes, based on the relationships of connections recorded in the gateways, with the actual communication routes. Moreover, by restricting the most appropriate network device managed by the gateway, the impact of the cyberattack can be minimized. Fujitsu Laboratories aims to commercialize these technologies during fiscal 2018 as part of the gateway functionality of the Fujitsu Network Virtuora series of network products, offered by Fujitsu Limited.
Development Background
Recent years have seen an increasing degree of IoT adoption in a variety of industrial fields, and as IoT devices, such as sensors and manufacturing equipment, have been connected to the network, cases of these IoT devices being damaged by malware attacks have occurred worldwide. This has created an urgent need for security countermeasures for IoT devices. In many cases, however, IoT devices do not support anti-virus software due to CPU, memory, or OS restrictions, and even if anti-virus software is deployed, often software updates that require the device to be rebooted are not executed as the IoT device cannot be stopped while in operation. Due to these factors, the current situation is that many IoT devices are operating with insufficient security measures.
Issues
In light of these problems, various consortiums and network device vendors have proposed measures using gateways to separate the network the IoT devices are connected to from the networks ordinary devices, such as PCs and servers, are connected to (Figure 1). This means that the gateway can protect the devices from cyberattacks from outside networks, but because cyberattacks can be conducted without going through the gateway if a devices infected with malware is connected inside the network the IoT devices are connected to, it was not possible to protect them from cyberattacks from infected devices.
https://www.acnnewswire.com/topimg/Low_FujitsuIoT52818Fig1.jpg
Figure 1: Existing technology: Network separation by a gateway
About the Newly Developed Technology
Now, Fujitsu Laboratories has developed technology that can collect operating information about IoT devices and network devices from gateway devices, deduce the topology(1) of the network the IoT devices are connected to, and appropriately control the network devices based on this information (Figure 2). With this technology, IoT devices communicating along routes not accounted for in the topology can be treated as unauthorized devices, enabling the technology to minimize the impact of cyberattacks by making those IoT devices unable to communicate with other IoT devices.
https://www.acnnewswire.com/topimg/Low_FujitsuIoT52818Fig2.jpg
Figure 2: Newly developed method
Features of the Newly Developed Technology
1. Topology management technology supporting devices with a variety of interfaces
This technology collects information from IoT devices and network devices about adjacent devices in a variety of formats, and then deduces the topology of the entire IoT network as it changes in real time. Because the different devices use a variety of interfaces having respective communication methods and data formats, this topology deduction is enabled by converting them all to a standardized interface in the gateway. With this technology, when IoT devices request an authorized communication route, the technology can collect the actual communication route from the network devices, discovering both unauthorized communications generated by cyberattacks and other issues, as well as the suspicious IoT devices that caused them, by comparing the authorized route with the actual route.
2. Network control technology that blocks communications from suspicious devices
Gateways can block communications between suspicious devices and other devices by controlling the network devices along the route using topology information. Because some devices use wireless, rather than wired connections, it is essential to control the appropriate network device, in a situation where communication pathways change moment to moment, and sometimes communications stop altogether. With this technology, it is possible to block communications by suspicious devices while minimizing the impact on communications of ordinary devices by selecting network devices while taking into consideration changes in topology and device status, and controlling those network devices per the connected device or a group of devices.
Effects
In a simulation using fake malware, Fujitsu Laboratories operated gateways equipped with this technology in coordination with existing network devices, and confirmed that this technology could block communications from suspicious devices. The results showed that this technology could minimize the impact of cyberattacks when installed in gateways. With this technology, it will be possible to provide secure operations using existing setups, without exchanging or deploying new IoT devices with security countermeasures in sites such as factories, which require the continued operation of production equipment with long service lifespans.
Future Plans
Fujitsu Laboratories aims to commercialize this technology during fiscal 2018 as a gateway feature in the Fujitsu Network Virtuora series of network products. In addition, it will continue to develop the technology, not just for the manufacturing industry, such as factories, but with a view toward expansion into a variety of industrial areas that require safe and secure management of IoT system operations.
(1) Topology The connection structure and profile, including specification information, for IoT devices and network devices
About Fujitsu Ltd
Fujitsu is the leading Japanese information and communication technology (ICT) company, offering a full range of technology products, solutions, and services. Approximately 155,000 Fujitsu people support customers in more than 100 countries. We use our experience and the power of ICT to shape the future of society with our customers. Fujitsu Limited (TSE: 6702) reported consolidated revenues of 4.5 trillion yen (US$40 billion) for the fiscal year ended March 31, 2017. For more information, please see https://www.fujitsu.com.
* Please see this press release, with images, at:
https://www.fujitsu.com/global/about/resources/news/press-releases/
Contact:
Fujitsu Limited Public and Investor Relations Tel: +81-3-3215-5259 URL: www.fujitsu.com/global/news/contacts/
Copyright 2018 JCN Newswire. All rights reserved. www.jcnnewswire.com

